Here, BENEDICT JOSEPH OLUWASEUN, with the following qualifications, B.Sc., MBA, M.Ed, M.Sc. Information Security & Digital Forensic, CISA, CISM, CRISC, CEH, PMP, ISO 27001 LA, and PMP, would throw some light on the aforementioned topic.
Cyber-related attacks have become increasingly imminent, and the severity and frequency of such incidents have grown significantly, resulting in severe damage to our global economy with no end. The estimated cost of cyber-attacks on the global economy in 2021 was about USD 6 trillion, which is estimated to be the GDP of the world’s largest economy and a new high of about USD 10.5 trillion annually by 2025 is predicted.
While the economy faces several cybersecurity threats, a more expensive, lethal, dangerous, and widespread type of phishing attack has grown silently but rapidly, drawing less attention to its catastrophic impact and costing businesses billions of dollars every year.
Business Email Compromise (BEC) also referred to as the ”Nigerian 419” scam is a specific and sophisticated spear phishing attack that focuses on legitimate businesses and persons to defraud them.
Email accounts of cooperate or public key employees or executives involved with financial transactions (such as wire payment transfers) in organizations are either compromised through key loggers, spoofed, or phished to carry out fraudulent payments resulting in billions of dollars in losses globally.
A report by GreatHorn revealed that spoofed email accounts or websites were the most experienced form of a BEC attack, as 71% of organizations acknowledged they had seen one over the past year. This is followed by spear phishing (69%) and malware (24%).
Rosenthal (2022) listed 14 reputable organizations that have been victims of BEC and also estimated that an average of $5.2 million was recorded as a loss per breach. For this reason, the FBI has named BEC a “$26 billion scam,” and the threat is increasing. BEC scams in 2020 alone recorded over &$1.8 billion compared to other cybercrimes.
Some of the Companies affected by BEC and their financial losses are:
- Facebook and Google: $121m BEC scam
- Ubiquiti: $46.7m vendor fraud
- Toyota 2019: $37 million BEC attack
- Obinwanne Okeke: $11 million in losses
- Scouler Co.: $17.2m acquisition scam
- Government of Puerto Rico: $2.6 million transfer
- Gift card scams
- Just to mention a few…
Source: https://www.tessian.com/blog/business-email-compromise-bec-examples/
In 2022, business email compromise (BEC) was unquestionably a successful tactic for fraudsters.
According to the most recent Internet Crime Report from the FBI’s Internet Crime Complaint Centre (IC3), businesses lost more than $2.7 billion as a result of these scams last year. That represents a $300 million increase from 2021. Additionally, these losses exceeded those brought on by ransomware by almost 80 times.
BEC scams actually accounted for a staggering 27% of all financial losses associated with cybercrime in 2022, according to the FBI’s IC3. Additionally, from $120,000 in 2021 to $124,000 in 2022, the average cost of each incident rose.
In 2022, there were fewer complaints made to the FBI’s IC3 (800,944 vs. 847,376). However, the total amount lost increased from $6.9 billion to more than $10.2 billion.
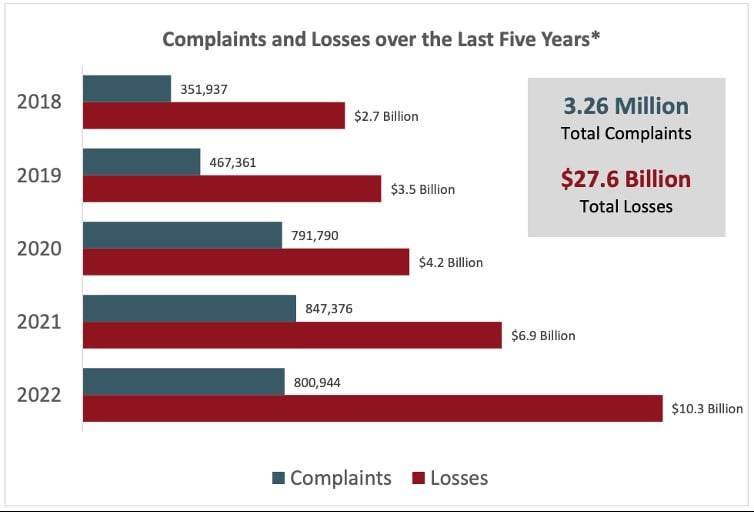
Reports of complaints and losses due to cybercrime over the previous five years.
(Image Source: FBI’s IC3 2022 Internet Crime Report.)
This surge in BEC attacks can be attributed to the new working culture practised during the COVID-19 pandemic, where individuals and organizations had to conduct daily business virtually. Joseph Carson, Chief Security Scientist, and Advisory CISO at Delinea, said, “In the situation where employees are required to work remotely, it becomes more challenging to verify with a colleague whether the request is legitimate, most especially in cases when the request looks urgent, people mostly fall for such scams.”
He further expressed concerns and challenges in proving BEC attacks were not human errors since criminals are highly skilled in hiding their tracks. Sharing a similar opinion, Andy Gill, Senior Security Consultant at LARES Consulting, states, “The record presented by the FBI Public Service Announcement doesn’t come as a surprise.
Also, claiming that the numbers may have been low since many BEC incidents may have been unreported and were swept under the rug”.
The fact that BEC attacks still maintain a high record of incidents to date implies that it is the most active form of attack used by cybercrimes.

Recommendations and Suggestions:
The weakest and strongest line of defence for any organization is its employees. With the increase in BEC attacks on a global scale and the evolving techniques and attacks by cyber criminals, organizations need to train their employees to become human firewalls. By doing this, they can identify and mitigate critical indicators of an attack before it’s too late.
Some other basic steps employees can take to safeguard against attacks:
- Zero Trust – irrespective of the familiarity between the sender and yourself, always verify every request to ascertain its legitimacy.
- Believe in yourself and take your time – Never be in a rush; if you notice any discrepancies in the request, then flag it.
- Check and recheck account information and other details for accuracy.
- Maintain company guidelines and procedures.
If you feel you have been compromised or fallen victim, report the breach immediately (to your management, bank, and local authorities) and follow up for resolution and reversal of the fraudulent transaction.
Organizations: As the reality of a remote working environment becomes a new normal, businesses and organizations need to implement and improve on their present security architecture, procedures, and protocols to protect the organization and its asset from spear phishing or other forms of attacks.
Once there is a disruption in the security protocols, employees will require guidance on verifying the credibility of financial requests or transactions. Some recommendations for protecting your employees from falling victim to BEC attacks are:
- Use multiple independent signatures for high-value transactions.
- Enable/add Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), Domain-based Message Authentication Reporting and Conformance (DMARC) to block spoofing messages, allow only authorized servers to send emails, and tell it what to do with the emails that haven’t cleared authentication.
- Implement strong account authentication (MFA) and password reset – to prevent unauthorized password resets and account logins.
- Only work with established vendor accounts to streamline transaction verification.
- Train employees to identify and prevent BEC attacks – this can be achieved by using simulations to give employees hands-on experience in identifying cyber-attacks.
- Develop an air-tight payment plan that will assist employees in identifying legitimate or illegitimate requests, such as mandating call verifications for individual transactions.
- Monitoring – regularly monitor all financial accounts for irregularities and verify all emails by enabling alerts for suspicious activity.
Cybersecurity is indeed a global risk; therefore, it requires a more collaborative and coordinated approach to address threats such as BEC, ransomware, data breach, denial-of-service attack, and phishing attacks. Global Risks to cybersecurity, privacy, data protection, and online safety need more attention.
Through intensive employee training, robust verification protocols, and email authentication, organizations can reduce and equip their employees with the skills required to identify and prevent attacks such as BEC.

